The following is an integrated model of a digital campus based on the IToIP thinking method:
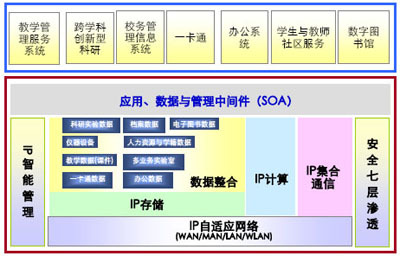
The bottom layer is the IP adaptive security network, which realizes the integration and penetration of the IP network and security.
Security and Optimization of Campus Basic Network
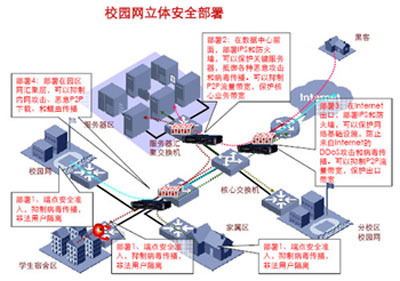
The security and optimization of the campus basic network is one of the main contents of the campus basic network integration. It is to achieve the security, smoothness and reliability of the campus network, and can provide core support for the upper-level key business. To achieve this, the entire network must be secure and reliable, from endpoint access to campus core to network exit. Three points depend on technology and seven points depend on management. Only through strong management and necessary technical means can the campus network be transformed from a loosely managed state.
The first is the access issue of endpoint devices. At present, the campus network has implemented an authentication management system for the user's identity, but it does not know the security status of the user's computer and cannot control the user's network behavior. The so-called secure access of the endpoint device is to be achieved. When the user's PC is connected to the network, the first is identity authentication to ensure that the user's identity is legal, and then the security status evaluation to check whether the user's operating system has vulnerabilities and patch problems. If it does not meet the security requirements, it will be quarantined. You can only go to the patch server to apply the patch and go to the virus server to upgrade the virus database. Then, the system issues security control policies to the access device to perform necessary control on the user's online behavior. Through these management and technical means, the security of the entire network system and the security of users themselves are guaranteed. This is the idea of ​​endpoint security access defense EAD.
In addition, it is necessary to ensure the security of network entrances and exits, and absolute security measures must be taken at the entrances and exits of campus networks and data centers. At present, in the campus network, various viruses are rampant, security attacks are rampant, and most of the attacks are based on the application layer. Traditional firewalls are based on three to four layers of detection and filtering, which can only deal with network layer attacks and ignore the security threats at the application layer. For example, on port 80 of HTTP, there is both legitimate traffic and attack traffic, and the firewall is powerless. How to deploy in-depth security defense equipment online to achieve real-time defense and security filtering while also matching the performance requirements of the network backbone? This requires the deep security defense solution TippingPoint IPS. Only by achieving close cooperation between the firewall and the active intrusion prevention system can the security of the campus network and applications be truly realized.
The following figure is a three-dimensional security deployment plan for campus networks, which truly realizes the ubiquitous security of campus networks and guarantees the security of campus core business and core resources.
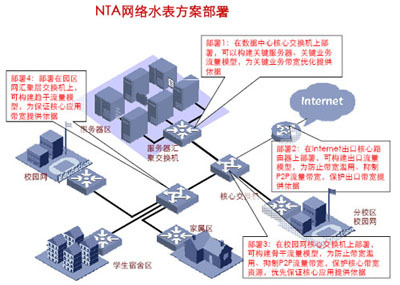
Third, in order to manage and optimize applications, the entire network needs to be changed from a black box network to a white box network. The campus network needs to have certain transparency. It is necessary to analyze large-scale network traffic. Through real-time status information collection and historical statistical information analysis, understand the network traffic distribution as a basis for implementing various optimization measures and QoS programs. Ensure the operation of core key business.
This is the NTA network flow analysis solution. The specific implementation measures are shown in the following figure:
The above three points are the contents of security penetration network. Through these technical optimizations in security and management, the robustness and manageability of the basic network are increased, and the basic network resources are guaranteed to support the school's core business.
Storage integration solution based on IP technology
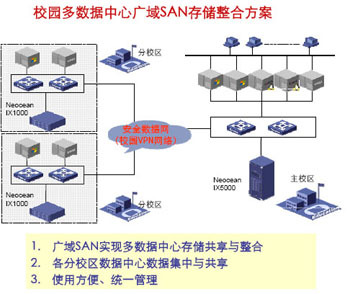
The following figure is a schematic diagram of data sharing and storage sharing in a multi-data center on a campus multi-data center through wide area storage technology. The technology used is the same as the above picture.
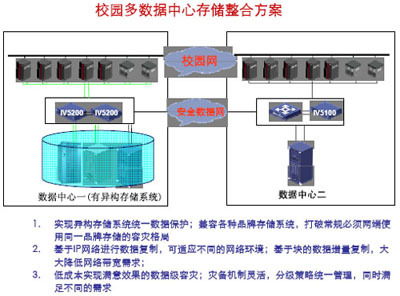
In the figure, the secure data network is a secure VPN network that is physically integrated and logically separated from the campus network. On the premise of fully ensuring data security, it can be reused as the campus's basic network because it is homogeneous with the existing campus IP network The resources greatly reduce the investment in infrastructure, and also solve the physical distance limitation (10 km) of the FC SAN storage system, and ultimately achieve satisfactory data backup and disaster recovery at low cost.
The following figure is a schematic diagram of data sharing and storage sharing in a multi-data center on a campus multi-data center through wide area storage technology. The technology used is the same as the above picture.
to sum up
In the past decade, education informatization has faced various challenges in terms of system, management and technology. In the development wave of education informatization in the future five to ten years, the integration and innovation of application systems, the integration of data, and the integration and optimization of IT basic resources will be the main contents of informatization construction in colleges and universities.
Large Capacity Gift Bag,Ldpe Wear Resistant Gift Bag,Customized Gift Bags,Daily Gift Bag
Dongguan City Diadia Industry Co.,Ltd , https://www.diadiabag.com